FAQ: Mobile Security and Samsung Project Infinity

Quick Navigation:
- What are the main vulnerabilities in mobile phones?
- How can operating system vulnerabilities impact mobile devices?
- What makes mobile applications a potential security risk?
- How do network vulnerabilities compromise security?
- What are hardware exploits, and why are they significant?
- How do phishing and social engineering attacks affect users?
- What is malware, and how does it impact mobile security?
- What causes data breaches on mobile devices?
- How does Samsung address these vulnerabilities through Project Infinity?
- What is the role of Samsung's Cyber Threat Intelligence (CTI) taskforce?
- How do the Red and Blue teams contribute to Samsung's security?
- What is the significance of the Purple team in mobile security?
- Why are Samsung's security updates essential for user safety?
- How does Samsung engage with external security researchers?
- What is Samsung Knox, and how does it enhance security?
- How does user awareness contribute to mobile security?
- What steps does Samsung take to ensure hardware security?
- Why is multi-factor authentication (MFA) recommended?
- How does Samsung monitor and address real-time threats?
- How does Samsung ensure collaboration across the cybersecurity ecosystem?
What are the main vulnerabilities in mobile phones?
Mobile phones are susceptible to a range of vulnerabilities, including operating system flaws, poorly coded applications, unsecured networks, hardware exploits, phishing, malware, and data breaches. These weaknesses can result in unauthorized access, data theft, and malicious control of devices. For more insights into these vulnerabilities and mitigation strategies, visit Samsung Mobile Security.
How can operating system vulnerabilities impact mobile devices?
Operating system vulnerabilities, such as zero-day exploits, allow attackers to manipulate devices remotely. For example, incidents like the Pegasus spyware attack exploited OS flaws to gain control over mobile devices.
What makes mobile applications a potential security risk?
Insecure or poorly designed apps may grant excessive permissions or include vulnerabilities in third-party libraries. Such flaws can expose sensitive data to attackers or inject malware into devices.
How do network vulnerabilities compromise security?
Using public Wi-Fi or networks with weak encryption exposes devices to man-in-the-middle (MITM) attacks. Such vulnerabilities can lead to intercepted data, stolen credentials, or unauthorized surveillance.
What are hardware exploits, and why are they significant?
Hardware exploits target device components like processors, compromising integrity and allowing attackers to bypass security measures. Examples include vulnerabilities like Spectre and Meltdown, which affected processors globally.
How do phishing and social engineering attacks affect users?
Phishing tricks users into divulging sensitive information, such as login credentials, by impersonating legitimate entities. Social engineering further manipulates individuals into installing malware or granting unauthorized access.
What is malware, and how does it impact mobile security?
Malware, including spyware and ransomware, compromises devices by stealing data, encrypting files, or granting attackers control. Preventing malware involves keeping software updated and avoiding suspicious apps or links.
What causes data breaches on mobile devices?
Data breaches often result from unsecured cloud storage, unencrypted backups, or stolen credentials. Mitigation requires encryption, secure storage practices, and awareness of potential risks.
How does Samsung address these vulnerabilities through Project Infinity?
Samsung’s Project Infinity is a multi-layered security initiative that includes regular updates, hardware-based protections, and real-time threat monitoring. It ensures comprehensive defenses against evolving threats. Discover more about this project at Samsung's Security Overview.
What is the role of Samsung's Cyber Threat Intelligence (CTI) taskforce?
CTI proactively identifies potential threats by monitoring deep and dark web activity for exploit discussions, malware tools, and stolen data. They address vulnerabilities before they become widespread.
How do the Red and Blue teams contribute to Samsung's security?
The Red team simulates hacker attacks to identify weaknesses, while the Blue team builds defenses and patches. Together, they form a robust offensive and defensive security strategy.
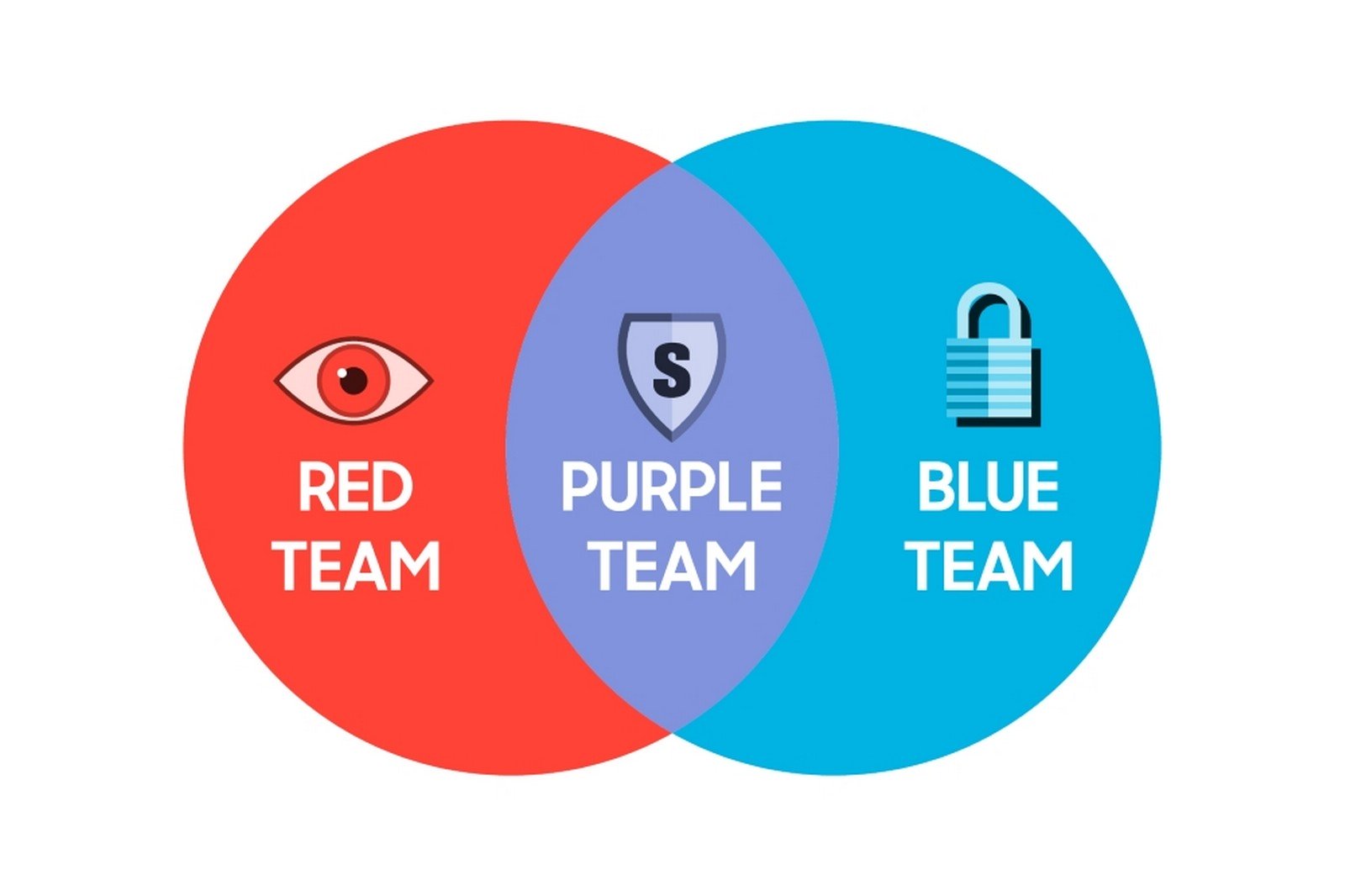
Credit: Samsung
What is the significance of the Purple team in mobile security?
The Purple team combines offensive and defensive expertise to protect critical Galaxy features. Their deep understanding of Samsung systems enables them to address vulnerabilities with precision.
Why are Samsung's security updates essential for user safety?
Regular updates address known vulnerabilities, safeguard against zero-day attacks, and enhance the overall security framework. With support extending up to seven years, Samsung ensures long-term protection for Galaxy users.
How does Samsung engage with external security researchers?
Through its Mobile Security Rewards Program, Samsung collaborates with researchers worldwide, offering rewards of up to $1 million for identifying severe vulnerabilities. Details are available at Samsung's Rewards Program.
What is Samsung Knox, and how does it enhance security?
Samsung Knox creates secure containers for apps and data, isolating sensitive information and protecting against unauthorized access. Knox is a cornerstone of Samsung's layered security approach.
How does user awareness contribute to mobile security?
Educating users about phishing, safe browsing practices, and recognizing suspicious activity reduces the risk of successful attacks. Awareness campaigns are integral to Samsung’s strategy.
What steps does Samsung take to ensure hardware security?
Samsung implements features like Trusted Execution Environments (TEE) and Secure Boot to safeguard against unauthorized tampering and hardware-based exploits.
Why is multi-factor authentication (MFA) recommended?
MFA adds a layer of security by requiring multiple verification methods, such as OTPs or biometrics, ensuring that unauthorized access remains unlikely.
How does Samsung monitor and address real-time threats?
Samsung's CTI taskforce uses advanced tools to trace Indicators of Compromise and identify the origin of threats, collaborating with developers to neutralize risks swiftly.
How does Samsung ensure collaboration across the cybersecurity ecosystem?
Samsung partners with chipset vendors, service providers, and the broader security community to identify and mitigate threats, enhancing the overall mobile security landscape.
We made FaqGuru.com to simplify understanding through FAQs. If you have questions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.
Comments powered by CComment